Center for Cybersecurity Analytics and Automation
National Science Foundation (NSF) Industry-University Cooperative Research Centers (IUCRC)
George Mason University

Current and Past Projects
The George Mason University site of the Center for Cybersecurity Analytics and Automation (CCAA) is operated by faculty at the Center for Secure Information Systems (CSIS).
For a complete list of our projects and capabilities please visit the CSIS website at http://csis.gmu.edu/. Below is a sample of current and past projects, in no particular order. A list of publications is also available on the CSIS website.
Select Projects
Defending Against Stealthy Threats: Advanced Persisten Threats
Advanced Persisten Threats (APTs) are sophisticated cyber attacks, often waged by state actors, organized crime, or other hostile organizations against high-profile targets. Their objective is to establish and expand their presence within target networks for the purpose of exfiltrating information and/or sabotaging critical aspects of a mission or organization. Every year, APTs steal millions worth of data and IP: APT1 alone stole hundreds of terabytes of data from 141 organizations. APT actors possess significant expertise and resources to operate in a stealthy mode over extended periods of time, adapting to a defender's strategies and evading detection.
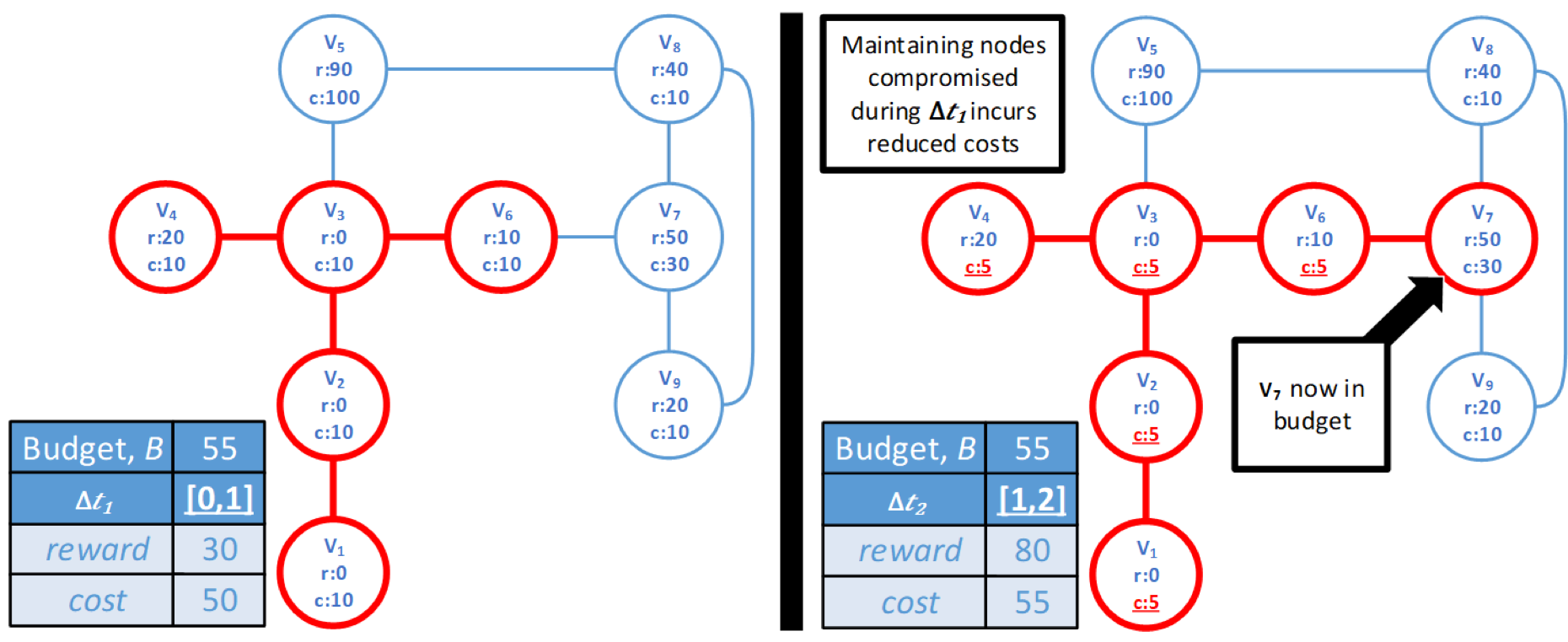
To overcome these challenges, this project aims at developing a model of the adversary that captures its behavior during reconaissance and lateral movement within the target network in terms of risk incurred and rewards gained by the attacker. Leveraging this model, we are developing defensive strategies, including approached based on deception, aimed at rendering the attacker's effort cost-ineffective.
DeBot: Detection and Mitigation of Botnets
Malicious actors use networks of compromised and remotely controlled hosts, known as botnets, to execute different classes of cyberattacks, including exfiltration of sensitive data. Recently, we have observed a trend toward more resilient botnet architectures, departing from traditional centralized architectures and enabling botnets to evade detection and persist in a system indefinitely. Botnets can achieve resilience through architectural stealth, by establishing overlay networks that minimize exposure of malicious traffic to detectors.
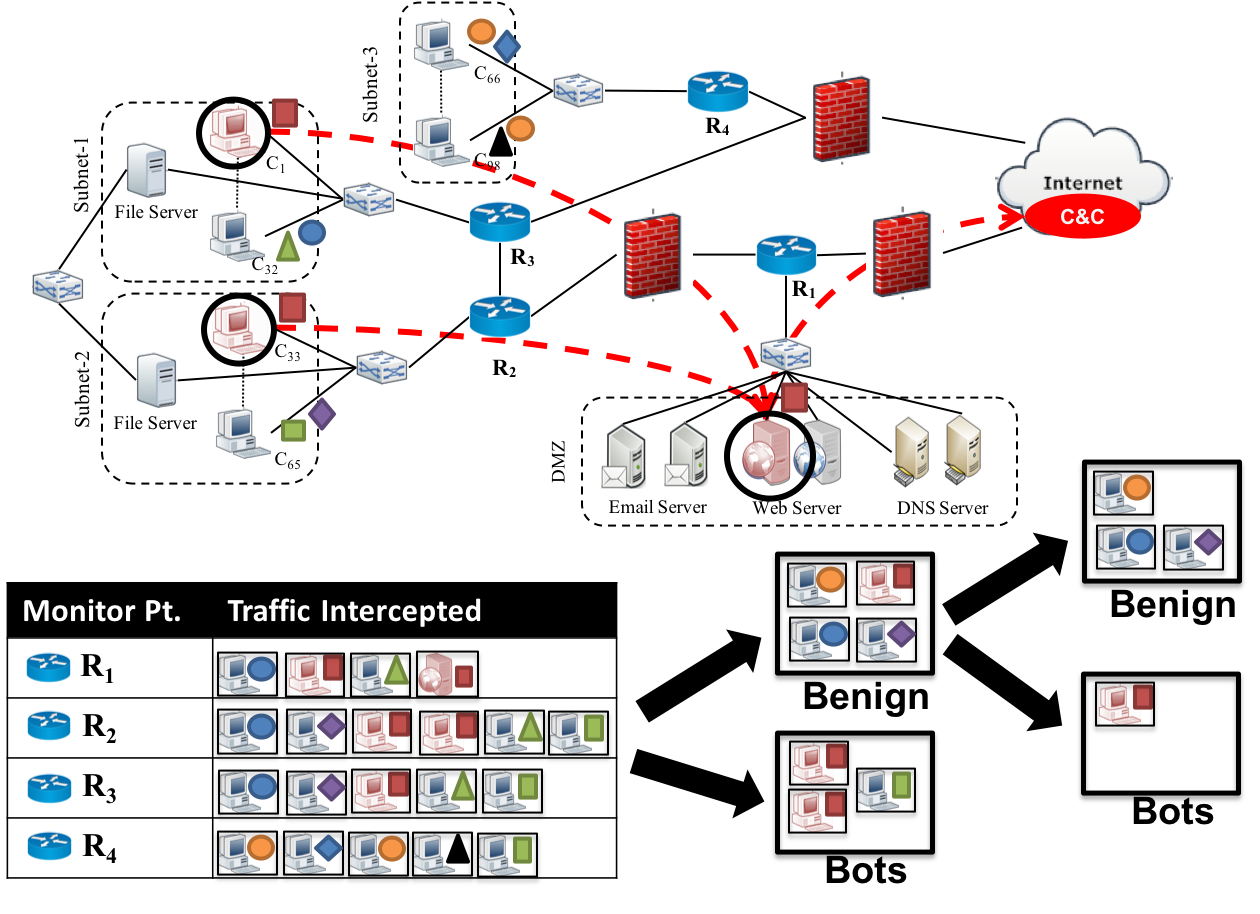
To address this problem, we propose a novel network-based detection scheme, called DeBot, which identifies traffic flows associated with exfiltration attempts. The proposed solution intercepts traffic from different monitoring points and leverages differences in the network behavior of botnets and benign users to identify suspicious flows. To this aim, we first develop a mechanism to identify monitoring points that are likely to intercept a significant volume of malicious traffic. Then, we analyze flow characteristics to identify suspicious hosts and use periodogram analysis to identify malicious flows originating from those hosts.We evaluate the proposed approach against different botnets in the CyberVAN testbed and compare its performance against state-of-the-art detection techniques. The results indicate that DeBot is effective in detecting botnet activity, thus enabling the identification and removal of bots.
Hardening Network Configurations in the Face of Zero-Day Vulnerabilities
To improve the security of complex networked systems and develop effective network hardening strategies, it is critical to consider the potential impact of zero-day vulnerabilities. Although known attack patterns can be easily modeled, handling zero-day vulnerabilities is inherently difficult due to their unpredictable nature. In fact, current approaches to network hardening only consider known vulnerabilities. As a consequence, the resulting hardening recommendations may be unrealistic and far from optimal. Additionally, most existing approaches assume that complete attack graphs have been generated, which may be unfeasible in practice for large networks.
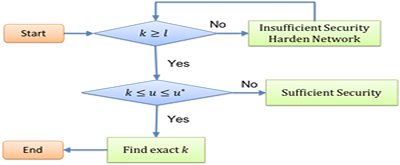
To overcome these limitations, we propose a goal-centric approach to network hardening that takes into account both known and zero-day vulnerabilities and only requires partial attack graphs. First, we propose to develop polynomial algorithms that, starting from a set of hardening goals, can build the partial attack graph that is relevant for the attacker to reach one of those goals. These algorithms must analyze known vulnerabilities and also hypothesize potential zero-day vulnerabilities. Second, leveraging our previous work on network hardening, we will develop polynomial algorithms that can identify sets of configuration changes that would prevent the attacker from reaching any of the goals considered.
SDN Security
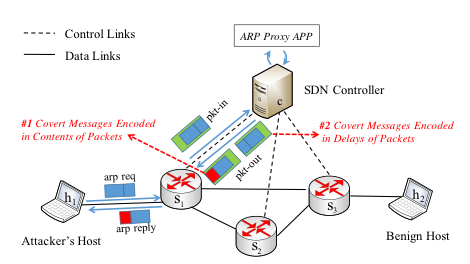
Software-Defined Networking (SDN) enables diversified network functionalities with plenty of applications deployed on a logically-centralized controller. In order to work properly, applications are naturally provided with much information on SDN. In this work, we study malicious applications that can exploit basic SDN mechanisms to build covert channels to stealthily leak out valuable information to end hosts, which are able to bypass network security policies and break physical network isolation. We design two types of covert channels with basic SDN mechanisms, a high-rate covert channel that exploits SDN proxy mechanisms to transmit covert messages to colluding hosts inside SDN and a low-rate covert channel that exploits SDN rule expiry mechanisms to transmit covert messages from SDN applications to any host on the Internet.
Open Source Software Security Analysis
Open-source and third-party software (OSS/TPS) has been widely deployed but not yet thoroughly tested for vulnerabilities. Depending on the critical nature of the software, appropriate measures are needed to assess the software for any security risk. Nowadays, it requires a large amount of human effort and expertise to manually analyze vulnerabilities. However, the explosive increase in the number of vulnerabilities in recent years poses a huge challenge to vulnerability tracking systems. To address this problem, we propose to develop a system that leverages the source code information extracted from the corresponding security patches to automatically identify the vulnerability type.
Security Analysis and Monitoring to Prevent Abuse of HPC Environments
The main objective of this project is to develop a security analysis and monitoring toolset that provides abuse prevention and malware detection solutions for HPCs and other similar systems to better assist end users (i.e., administrators, cyber analysts) in program security analysis. We will help identify a list of representative vulnerability types and collect malware that exploit the related vulnerabilities and user example malware to demonstrate 0-day attacks. We will also develop a machine learning based toolkit to classify different vulnerability types.
Hands-on Ethical Hacking Course Materials
Training and certifications are critical to industry but often lack hands-on experience. This project was designed to bridge the gap between theory and practice, and aimed at developing hands-on materials for a course on Ethical Hacking and Pen Testing. Materials developed under this project include a course description, learning objectives, PowerPoint presentations, instructor notes in PowerPoint format, practical components with hands-on lab exercises, pre-course and post-course assessments, and comprehensive practical assessment to determine level of learning and appropriateness of content against learning objectives. The course was developed jointly with customers to meet their training and certification objectives. Materials developed under this project are available at http://csis.gmu.edu/ehc/. Please contact us to obatin access credentials.
For a complete list of our projects, capabilities, and publications please visit the CSIS website at http://csis.gmu.edu/.